Controlling who accesses specific data within your organization is vital for security, compliance, and data governance. While New Relic's role-based access control manages what features users can access, data access control manages what specific data users can view.
Currently, data access control is available for log data, allowing you to restrict user access to specific log partitions.
How it works
Large organizations generate massive amounts of logs across various teams, services, and environments. Security teams need to monitor critical security logs that may contain personally identifiable information (PII), while development teams only need to see logs relevant to their specific microservices. Data access control lets you create policies that define exactly which log partitions each team can access.
You create data access policies that restrict access to specific log partitions and assign them to user groups via access grants. Users in groups with assigned policies can only access the log partitions allowed by those policies.
We recommend starting with a deny-all approach and then adding allow policies to grant access only to necessary partitions. This follows the principle of least privilege and ensures users only access data they need.
Key concepts:
- Data access policies: Define which log partitions users can access using allow-lists or deny-lists.
- Policy assignment: Policies are assigned to groups via the *Access Management** UI.
- Wildcard matching: Use
%as a wildcard to match multiple partitions (e.g.,log_prod%matches all partitions starting with "log_prod"). - Multiple policies: When users belong to multiple groups with different policies, the most permissive access applies.
Importante
Users with restricted access might still see information from restricted log partitions through historical exports, alert notifications, or the Insights API. See potential data exposure risks for details and mitigations.
Requirements
To create and manage data access policies, you must have:
- Pro or Enterprise edition account
- Authentication domain manager role
- Core user or full platform user type
Create and assign data access policies
You can create and assign data access policies through the UI or the NerdGraph API. To create a policy through the UI, refer to the following steps:
Create a policy
- Go to one.newrelic.com > Administration > Access Management > Data access policies.
- Click Create a policy (or Add a policy if you have existing policies).
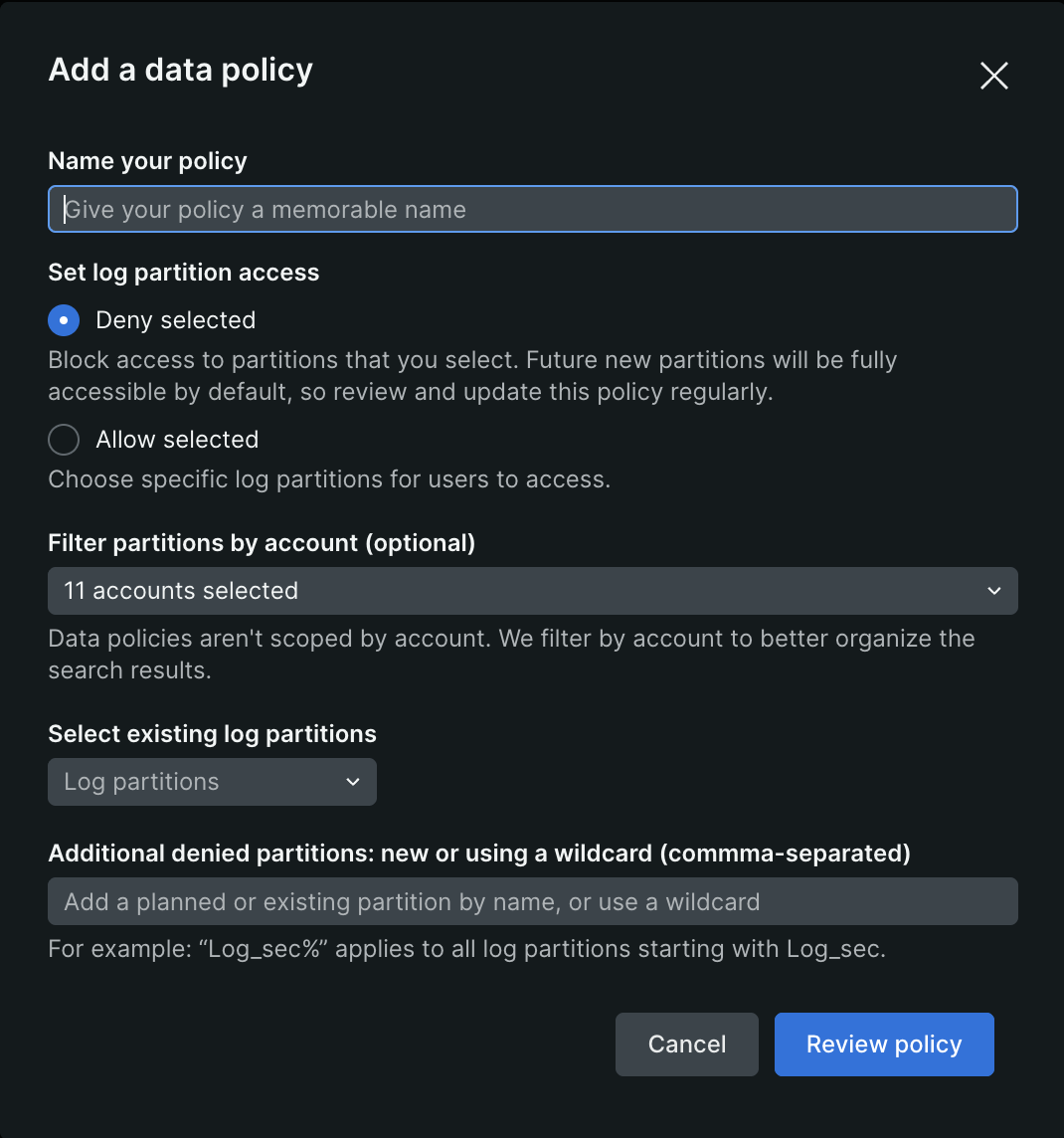
- Enter a name for the policy.
- Select a condition:
- Deny selected: Blocks access to selected log partitions.
- Allow selected: Allows access only to selected log partitions.
- From the Filter partitions by account dropdown, select accounts to shortlist the log partition list.
- Select log partitions to include in the policy:
- Choose partitions from the dropdown, or
- Type partition names or wildcards (e.g.,
log_go%to match multiple partitions), separated by commas.
- Click Review policy to verify your configuration.
- Click Create policy.
The policy appears in the Data access policies tab. To view, edit, or delete it, click the menu.
Assign the policy to a group
- Go to Administration > Access Management > Grants.
- Find the grant to assign the policy, then click the menu next to it.
- Select Add data access policy.
- From the Policies dropdown, select your policy.
- Click Save.
The Policy name column shows the assigned policy. To remove or change it, use the menu.
Potential data exposure risks
While data access control restricts log data access in most New Relic features, there are scenarios where users might still see restricted data:
Related topics
User management concepts
Learn about user types, roles, and user management capabilities.
Manage users with NerdGraph
Use the NerdGraph API to programmatically manage users and access grants.
Log partitions
Understand how to organize your log data into partitions for better control and performance.
Manage data access policies via NerdGraph
Learn to create and manage data access policies using the NerdGraph API.